“COVID-19” and “coronavirus” email scams have nearly tripled in the past week: SophosLabs

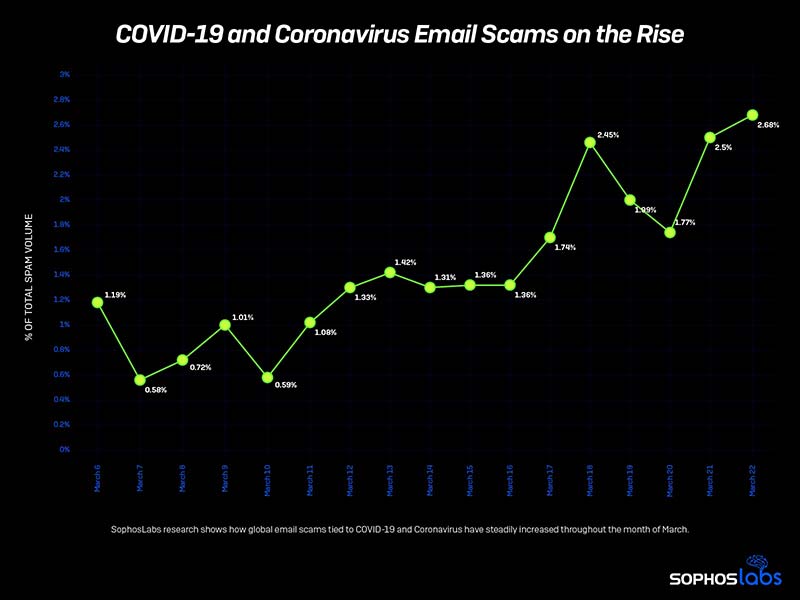
Sophos, a global leader in next-generation cloud-enabled cybersecurity solutions, in a recent live report stated that the volume of “COVID-19” and “coronavirus” email scams have nearly tripled in the past week. The live report publishes indicators of compromise Sophos discovers for related threats where in-house cybersecurity experts examine some of the trends they are seeing in pandemic-themed spam and scams.
According to Sophos, unscrupulous marketers and cyber-criminals have seized upon concerns over the emergence of the COVID-19 global pandemic as bait for spam, phishing attacks and malware. In recent weeks, the use of “coronavirus” and “COVID-19” in domain names, potentially unwanted email messages, and phishing and malware delivery schemes has skyrocketed.
“While COVID-19 emerged as a crisis in China in December, references to the virus in spam and phishing emails only really began to emerge in January—and like the virus itself, they grew exponentially. By early March, COVID-19 and Coronavirus already represented a significant percentage of the spam traffic we measured,” reveals the report titled “Facing down the myriad threats tied to COVID-19.”
Attackers are also increasingly impersonating the WHO (World Health Organization), CDC (Centers for Disease Control and Prevention, North America) and the United Nations (UN), as evidenced in scams tracked by SophosLabs.
Sophos Principal Research Scientist Chester Wisniewski said, “Cybercriminals are wasting no time in shifting their dirty, tried and true attack campaigns toward advantageous lures that prey on mounting virus fears. It is easy to see, for example, that the attackers behind a new Chloroquine scam are the same as those behind a recent herbal Viagra scam.”
“With global spam volumes estimated to be in the hundreds of billions, for 2-3% of those to be COVID-19 themed is significant. Similar to A/B testing of advertisements and web pages, criminals often dip a toe in the water when there is a new or sensational topic in the news. If the new topic proves a more effective lure than the previous scam bait, they begin switching to new lures,” he said further.
One of the spam campaigns Sophos tracked this week showed evidence that criminals had been using fake shipping and delivery emails to convince unsuspecting victims into opening attachments and infecting their computers with the Kryptik Trojan. The main body of the email pretends to come from erecruit@who.int with “health advice” in the attachment, but when carefully inspected the plain text body, Sophos found out that it matched a previous spam campaign from this same criminal using a lure pretending to be about invoices and deliveries.
The increases Sophos is seeing are likely due to two important factors, said Wisniewski. “First, as time passes more and more criminal groups are joining the party on using all this interest in COVID-19 to steal money from people. Secondly, it takes time. Any given criminal group has to handcraft the spams to convince the recipient to take action. In the research community, we call this the call to action. The call to action might be to open the attachment, visit the website or, in the case of the WHO Bitcoin scam (attached), to donate cryptocurrencies to criminal controlled Bitcoin wallets. Crafting these messages takes time, especially for those who are not native English speakers.”




